Authentication Server Function [1]¶
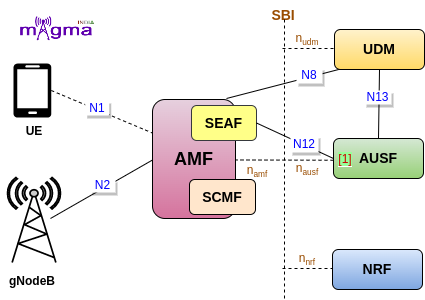
AUSF is a Control Plane(CP) function, and as its name sounds, it manages the authentication-related procedures in the 5GS(5G System). It provides a UE authentication service to the AMF and derives cryptographic keys to protect the signaling and user plane data. It is connected with the AMF and UDM through SBI(Service Based Interface).
Authentication Procedure¶
Sending Temporary Identifier¶
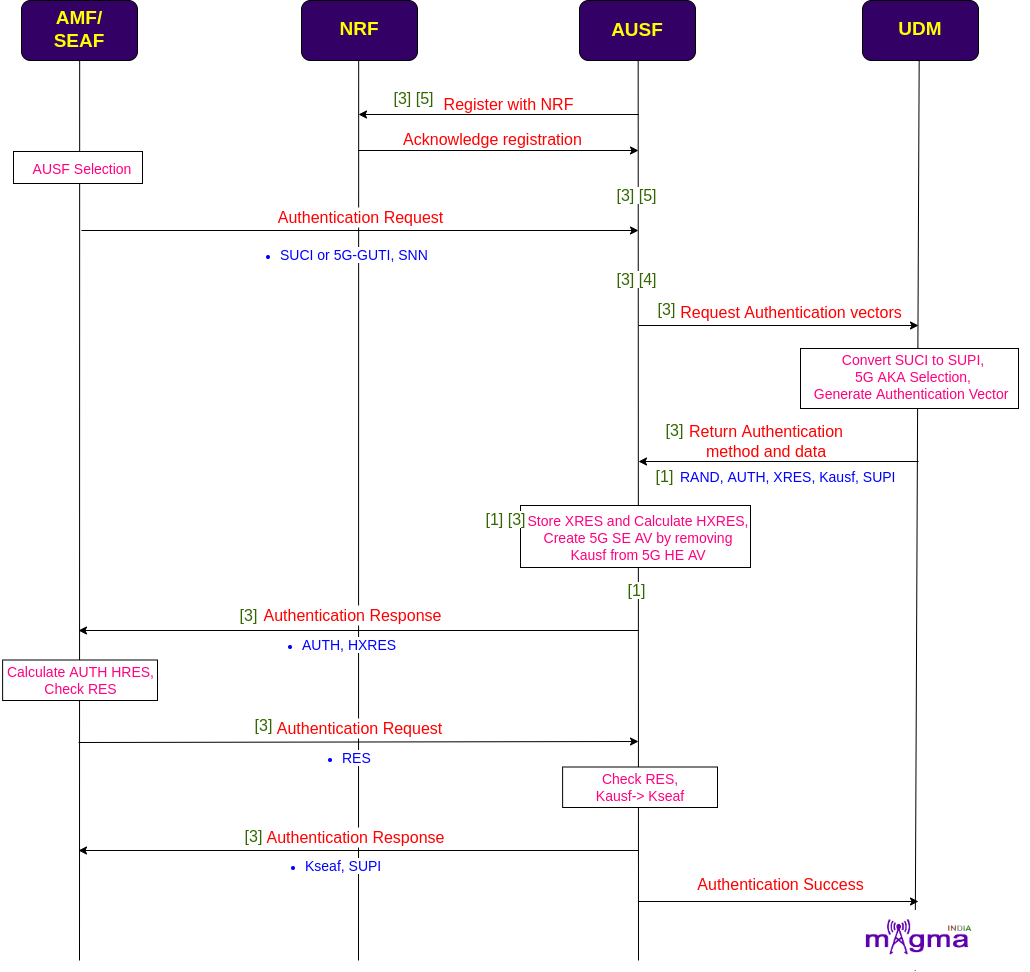
On receiving the registration request by the AMF, it chooses the best AUSF in the network for serving the user and initiates an authentication process in which a temporary identifier such as SUCI or 5G-GUTI and SNN(Service Network Name) is sent to the AUSF. AMF won’t be able to find the AUSF URL without NRF so the AUSF must be registered with it before the authentication starts.
AMF is not involved directly in the authentication procedure, it communicates with the AUSF through SEAF(Security Anchor Function). AUSF then requests the authentication vector from the UDM. UDM converts the SUCI to SUPI, generates authentication vectors, and selects 5G AKA as the authentication procedure.
Retrieving Authentication Parameters¶
The authentication data received from the UDM is used by the AUSF to derive the authentication vector, different keys, and necessary authentication parameters from the UDM. The AUSF then stores XRES(Expected Response), calculates HXRES(Hash of the Expected Response token) from it, and creates SE(Serving Environment) AV(Authentication Vector) from HE(Home Environment) AV.
The AMF sends the AUTH token, HXRES in the authentication response to the SEAF. The SUPI is not sent to the SEAF in this response, it is only sent to the SEAF after the UE authentication succeeds. The SEAF stores the HXRES and sends the AUTN in an authentication request to the UE. The UE validates the AUTN by using the secret keys and if the validation succeeds, it sends the RES token to the SEAF, which is validated by the SEAF. Upon successful validation, it is last sent to the AMF, to validate RES and end up with some authentication conclusion. If the RES is valid, it derives an anchor key Kseaf to send it to the SEAF, along with the SUPI. AUSF also informs the UDM about the authentication completion.
Deriving Keys¶
Upon receiving the Kseaf, the SEAF derives the Kamf(AMF Key) to send it to the AMF. SEAF also deletes the Kseaf before sending the AMF key. The AMF derives the Kamf to protect the signaling messages between the UE and AMF and Kgnb(gNB key) is derived to send it to the gNB. gNB derives the Kgnb to protect the communication that takes place between the UE and the gNB. The UE can derive all the above keys to access the network resources.
[5] send NF registration request with NRF
[4] AUSF config NRF
[5] Generate AUSF profile
[4] Config AUSF
[4] config AUSF SBI
[2] Get Authentication info
[4] AUSF config UDM
[3] Create authentication to send to UDM
[3] Send a request to UDM
[3] Getting parameters from UDM
[3] Get authentication-related info
[1] Derive Kausf
[1] Generate Vector
[1] Generate AUTN
[1] Derive SQN MS
[1] Generate RAND
[1] Generate HXRES
[3] Generate HXRES*
[3] Generating 5G AV from 5G HE AV
[3] Send authentication context to SEAF
[3] Handle UE authentication
[3] Handle UE authentication confirmation
[3] Send Kseaf to SEAF
[3] Set context id to the security context
[3] Set SUPI to the security context
[1] Derive Kseaf
[1] Derive Kamf
[1] Derive Knas
[1] Derive Kgnb
[3] Get info from the security context stored in AUSF